Stop cost spikes
Caps, budgets, alerts
Enforce project budgets and token caps before provider spend runs away.
ENTERPRISE LLM GATEWAY
OpenAI-compatible gateway for budgets, PII guardrails, audit logs, and reliability routing.
POLICY • AUDIT • BUDGETS • ROUTING
Cloudflare-native edge
Policy decisions • Request trace timeline • Budget actions
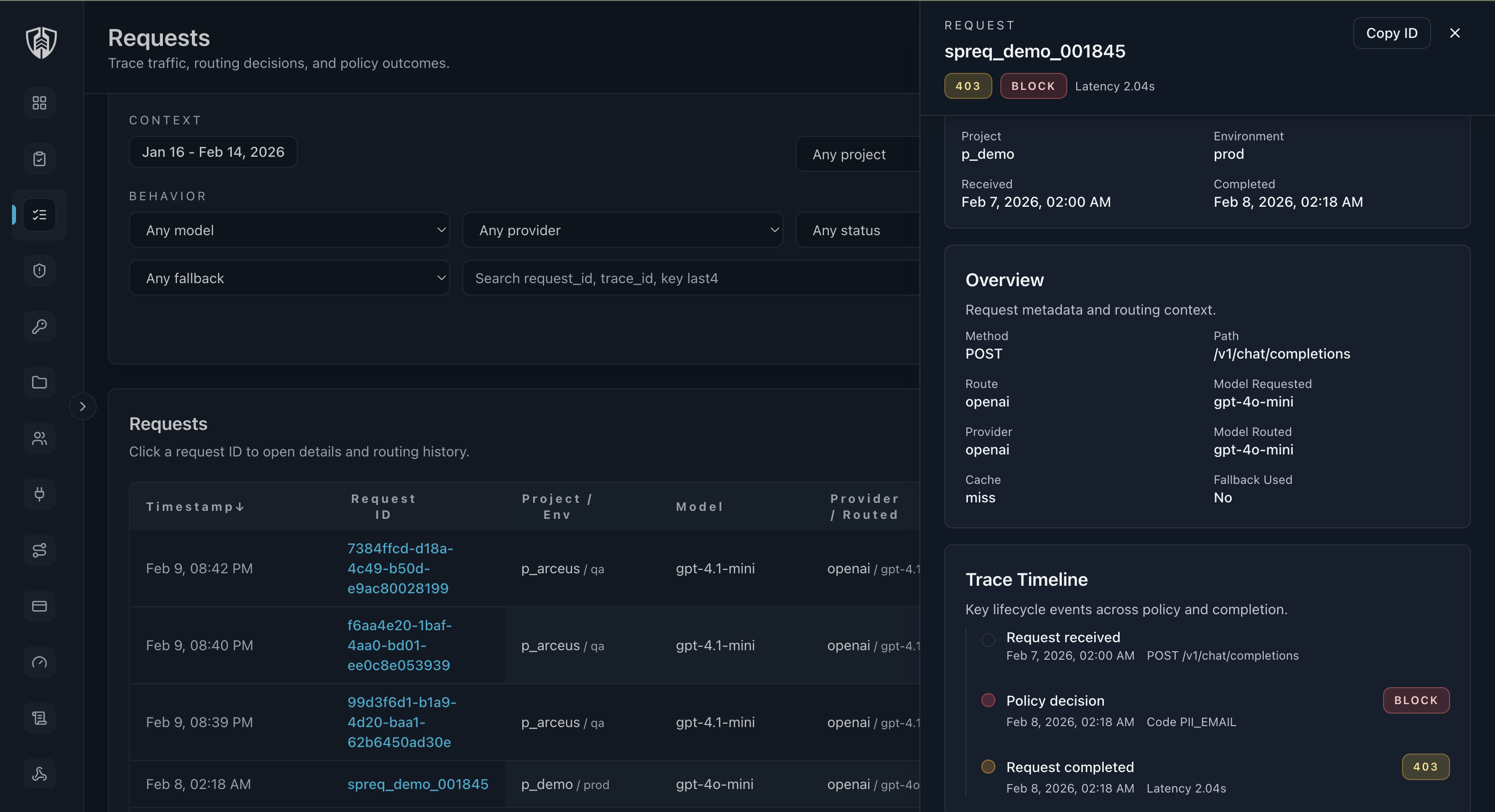 PII detected -> blocked
PII detected -> blockedCaps, budgets, alerts
Enforce project budgets and token caps before provider spend runs away.
Redact / block before storage
Apply redact or block decisions at ingress so sensitive data does not leave your boundary.
Retry + fallback routing
Fail over cleanly with retry and fallback policies when primary routes degrade.
Who this is for
Standardize LLM ingress without SDK rewrites across services.
Apply policy controls and preserve auditable request evidence.
Enforce budgets and stop runaway token spend before invoices.
Core capabilities
Set monthly and per-project spend caps with deterministic enforcement actions.
Budget view
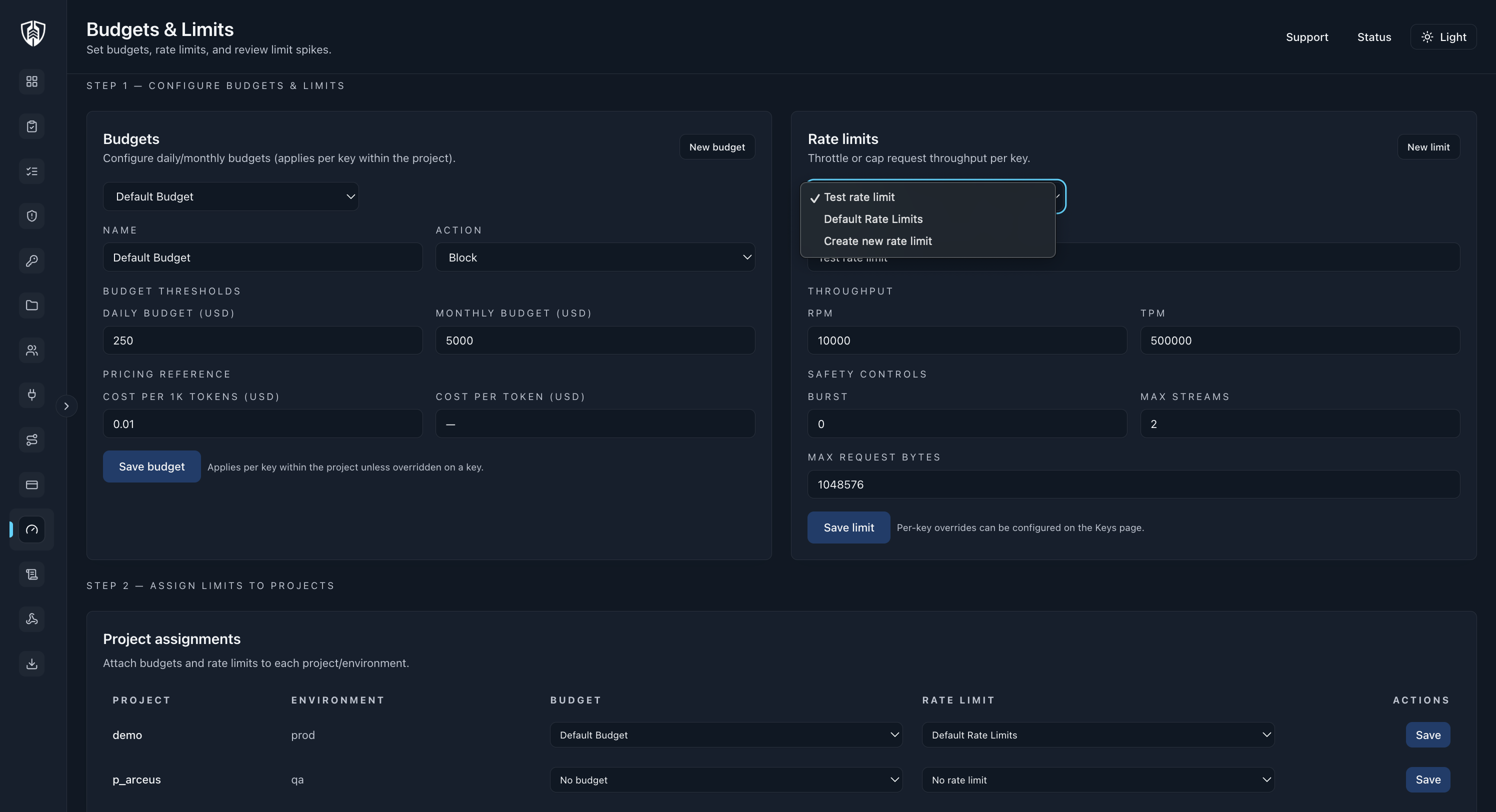
Threshold alert at 80%, hard block at 100%.
Control throughput by tenant, project, and key profile.
Evaluate content for sensitive entities and redact or block automatically.
Keep provider keys isolated and rotated with scoped project controls.
Export structured audit records on configurable retention profiles.
Map logical models to multiple providers with retry and failover.
Track latency, tokens, and cost by environment and team.
Reduce duplicate spend with policy-aware response caching.
How it works
Step 1
Keep your existing OpenAI SDK flow and point requests to Sentinel Primo.
Step 2
Run allow, block, and redact checks before provider execution.
Step 3
Review audit logs, budget actions, route decisions, and reliability outcomes.
Routing diagram
Control-plane proof
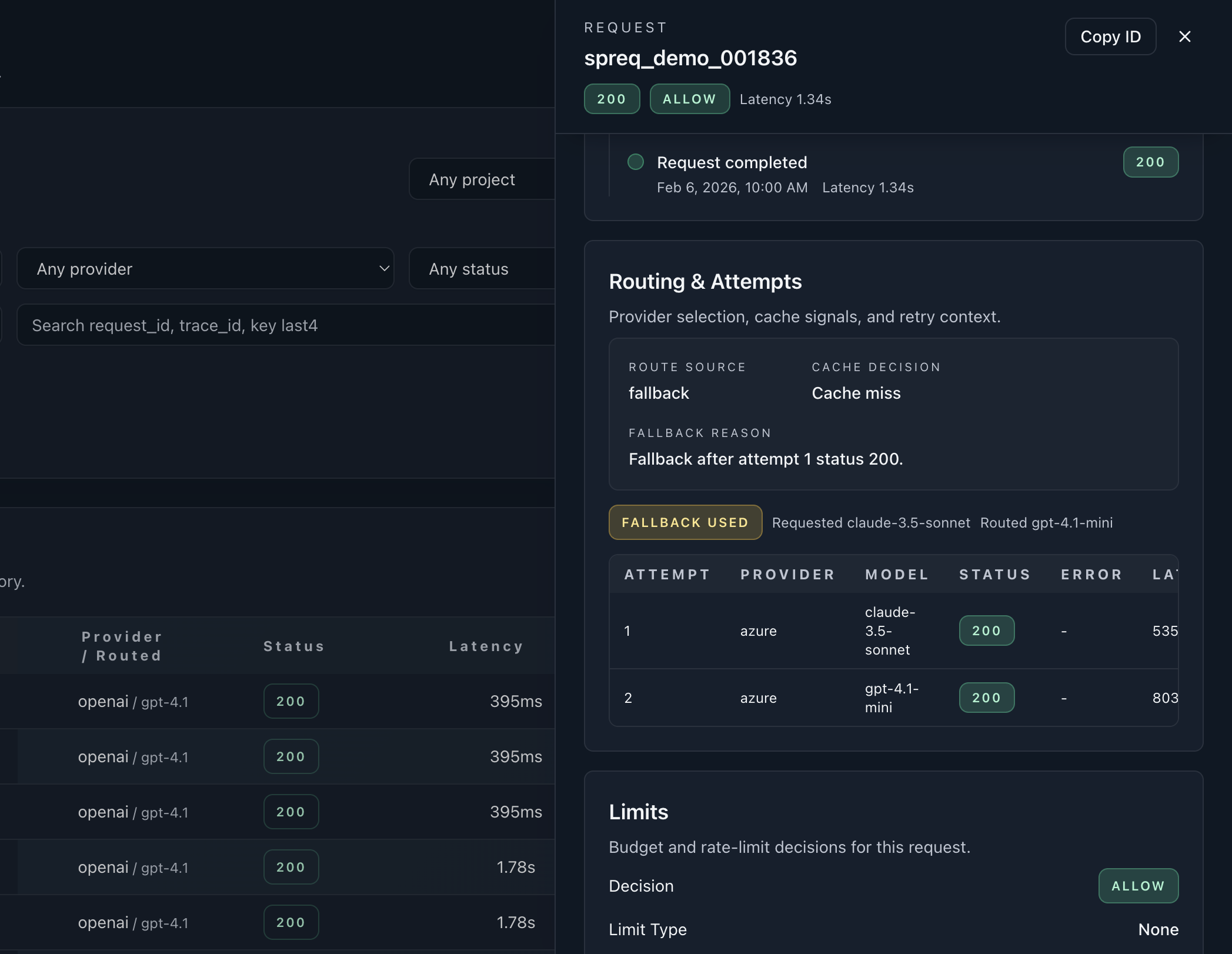
Live request queue with policy and route outcomes.
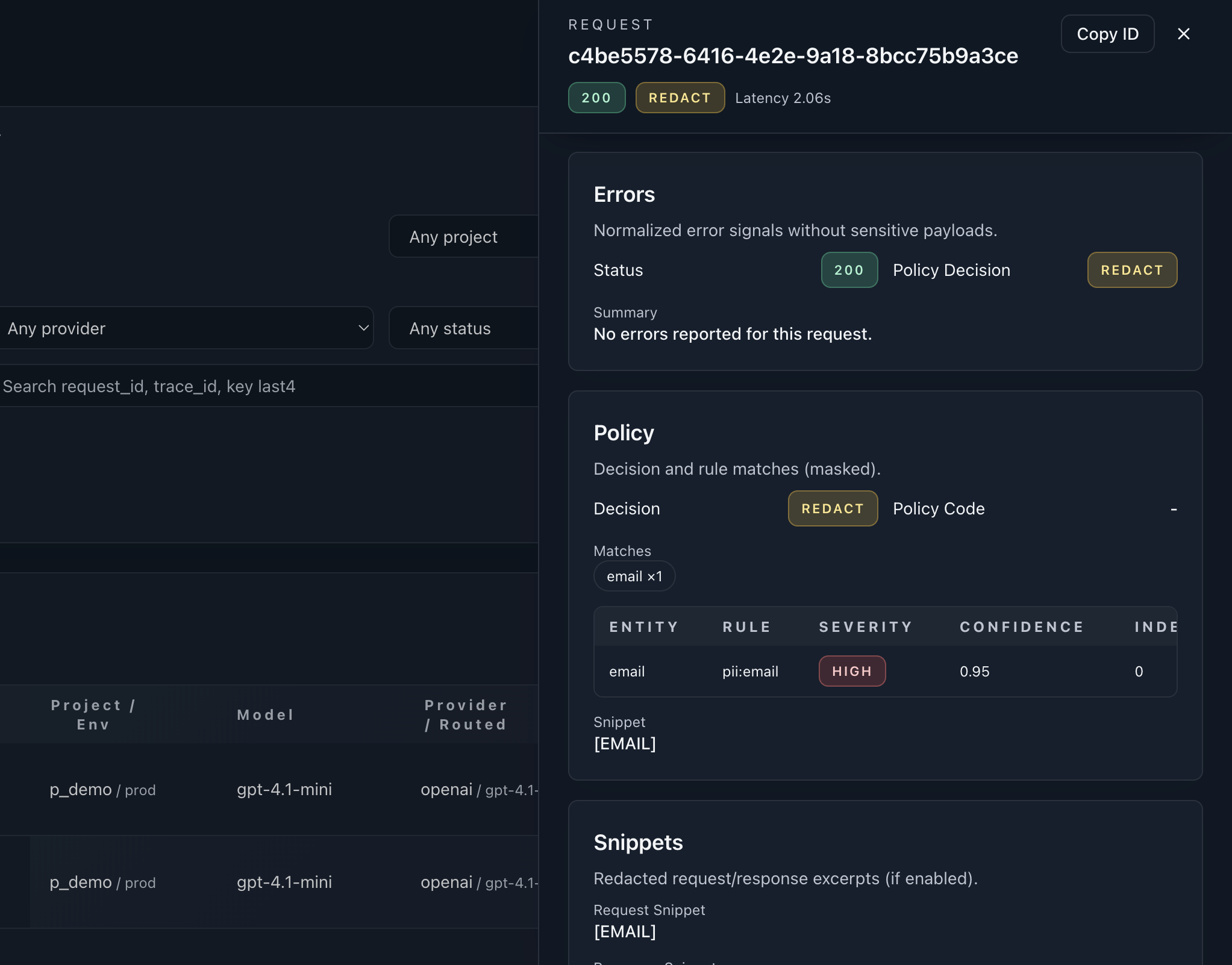
Deterministic policy path with redact and block evidence.
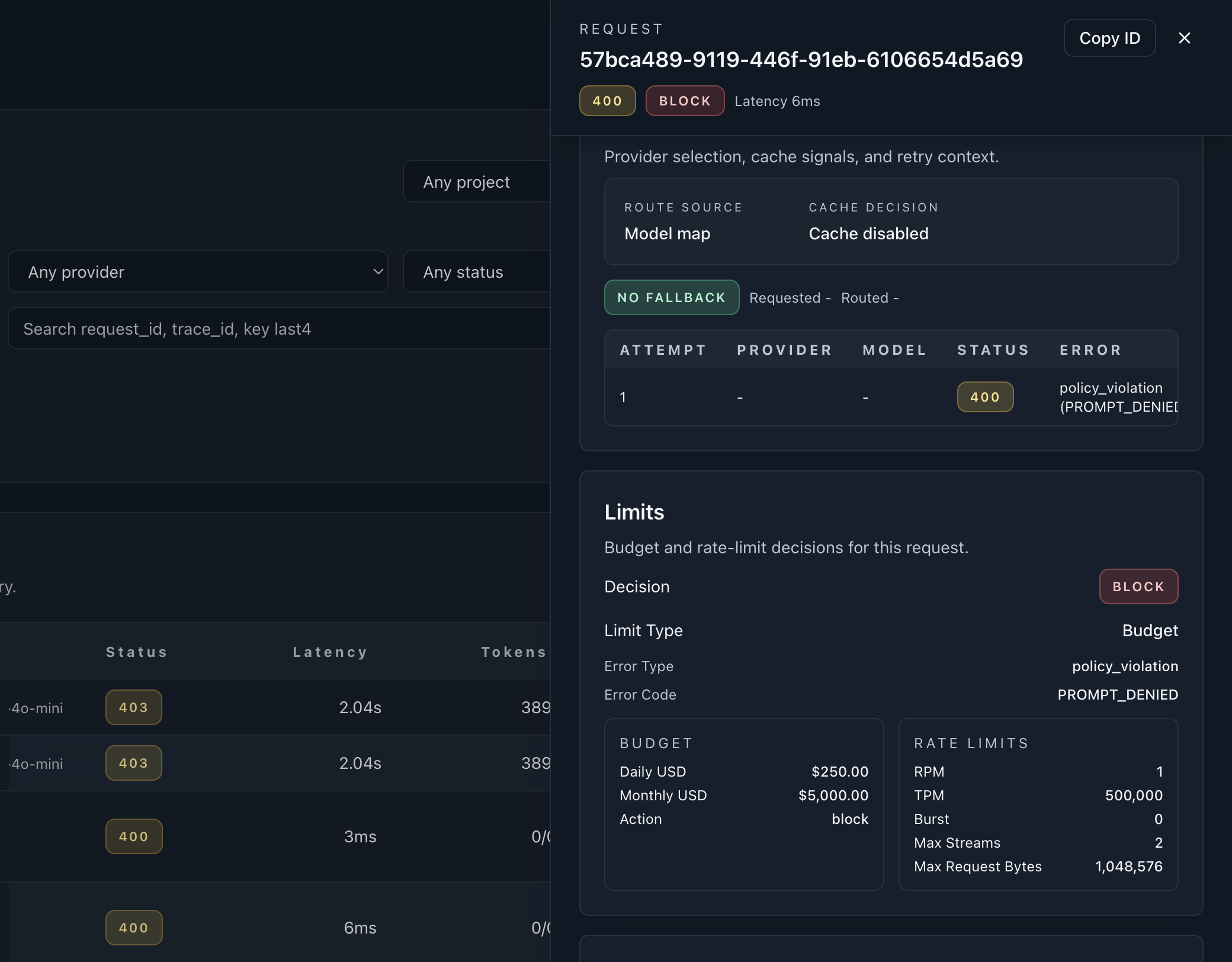
Budget governance with threshold and enforcement signals.
Security & trust
Not by default. Sentinel Primo is designed around metadata-first logging and configurable retention controls.
Policies can detect sensitive entities and apply allow, redact, or block actions before provider forwarding.
Yes. Retention profiles are configurable so teams can align operational visibility with internal policy.
No. Provider credentials stay server-side inside Sentinel Primo policy and routing layers.
Yes. Structured audit exports are available for compliance, finance, and security workflows.
Resources
Swap your base URL, verify request flow, and enable baseline policy checks.
Define spend guardrails and enforce deterministic budget actions.
Design retry and fallback behavior for provider outages and latency spikes.
Configure PII treatment, metadata logs, and retention posture.
Early-access pricing is available for design partners. Request a demo to discuss fit.
Talk to salesReview architecture fit, policy posture, and rollout sequencing with the Sentinel Primo team.